Register now to gain access to all of our features. Once registered and logged in, you will be able to create topics, post replies to existing threads, give reputation to your fellow members, get your own private messenger, post status updates, manage your profile and so much more. If you already have an account, login here - otherwise create an account for free today!

How to crack Apps on iOS 11
#41
 Posted 20 March 2018 - 08:51 AM
Posted 20 March 2018 - 08:51 AM

#42
 Posted 20 March 2018 - 09:09 AM
Posted 20 March 2018 - 09:09 AM

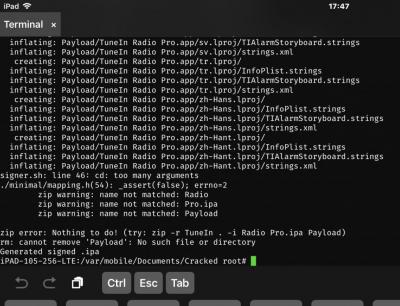
@Bontek, I updated the ghostbin code, I will try TuneIn again. This error occurs because the $EXECUTABLE variable wasn't/isn't a string, making it try to zip up "Radio", but not "Radio Pro.app". Try again and tell me the results.
EDIT: Okay, I tried two apps this time, TuneIn Radio and a Tones.app and they both worked after cracking with sacmunCrack, so It *should* work for you hopefully.
#43
 Posted 20 March 2018 - 10:08 AM
Posted 20 March 2018 - 10:08 AM

#44
 Posted 20 March 2018 - 10:14 AM
Posted 20 March 2018 - 10:14 AM

#45
 Posted 20 March 2018 - 10:56 AM
Posted 20 March 2018 - 10:56 AM

WOW !!!!! NOW IS WORKING PERFECT thanx bro@Bontek, NO! Use this one: https://ghostbin.com/paste/znzvp
FFS SMH TBH FML KMN
Well patched and re-packed.....installed without problem and starting no crash....
So its time that i could now play my loved GRID
Thanx again SACMUNRAGA - I CAN CONFIRM : YES - THIS CRACK IS WORKING FINE!!!!
- Sacmunraga likes this
#46
 Posted 17 April 2018 - 05:53 AM
Posted 17 April 2018 - 05:53 AM

/private/var/mobile$ bash bfinject -P XXXXX -L decrypt [+] Electra detected. [+] Injecting into '/var/containers/Bundle/Application/9EDDE92B-07DA-4F5D-85AD-6780D38DE83A/XXXXX.app/XXXXX' [+] Getting Team ID from target application... [+] Thinning dylib into non-fat arm64 image [+] Signing injectable .dylib with Team ID 1234567 and platform entitlements... [bfinject4realz] Calling task_for_pid() for PID 361. [bfinject4realz] Calling thread_create() on PID 361 [bfinject4realz] Looking for ROP gadget... found at 0x1853274e0 [bfinject4realz] Fake stack frame at 0x108a6c000 [bfinject4realz] Calling _pthread_set_self() at 0x185567804... [bfinject4realz] Returned from '_pthread_set_self' [bfinject4realz] Calling dlopen() at 0x185327460... [bfinject4realz] Returned from 'dlopen' [bfinject4realz] Success! Library was loaded at 0x1c41f8a00 [+] Decrypting App on Device ... [+] This may take up to a minute to finish, please wait ... [*] Moving the Decrypted IPA ... decrypted-app.ipa [+] If you see decrypted-app.ipa above we are almost done ... [+] Attempting to unzip .ipa [+] Adding cracker credentials to the App [+] Attempting to sign XXXXX with LDID [+] Attempting to zip and rebuild the .ipa [+] Signing completed successfully [+] Generated signed .ipa in /var/mobile/Cracked/XXXXX.ipa [*] Done, make sure to test the app
#47
 Posted 17 April 2018 - 07:00 AM
Posted 17 April 2018 - 07:00 AM

#48
 Posted 17 April 2018 - 07:08 AM
Posted 17 April 2018 - 07:08 AM

@user_hidden nice. Did you do some modding to the script?
if i was part of github i'd push changes to your script
send me over a PM, i should be back later today
- quangcaofgs likes this
#49
 Posted 12 July 2018 - 03:31 AM
Posted 12 July 2018 - 03:31 AM

I'm not able to access the ghostbin link, can you paste the shell somewhere else?
I'm trying to use bfinfect with 7wonders.app. The app is installed in the device, but when I run it, it crashed, so the ps command doesn't find it into the active processes.
So I modified the shell bfinfect to allow -D parameter to find the app path into the device, like that:
#!/jb/bin/bash
CYCRIPT_PORT=1337
function help {
echo "Syntax: $0 [-p PID | -P appname | -D DirectoryName] [-l /path/to/yourdylib | -L feature]"
echo
echo For example:
echo " $0 -P Reddit.app -l /path/to/evil.dylib # Injects evil.dylib into the Reddit app"
echo " or"
echo " $0 -p 1234 -L cycript # Inject Cycript into PID"
echo " or "
echo " $0 -p 4566 -l /path/to/evil.dylib # Injects the .dylib of your choice into PID"
echo
echo "Instead of specifying the PID with -p, bfinject can search for the correct PID based on the app name."
echo "Just enter \"-P identifier\" where \"identifier\" is a string unique to your app, e.g. \"fing.app\"."
echo
echo Available features:
echo " cycript - Inject and run Cycript"
echo " decrypt - Create a decrypted copy of the target app"
echo " test - Inject a simple .dylib to make an entry in the console log"
echo " ispy - Inject iSpy. Browse to http://<DEVICE_IP>:31337/"
echo
}
#
# check args
#
if [ "$1" != "-p" ] && [ "$1" != "-P" ] && [ "$1" != "-D" ]; then
help
exit 1
fi
if [ "$3" != "-l" -a "$3" != "-L" ]; then
help
exit 1
fi
if [ "$1" == "-p" ]; then
PID=$2
elif [ "$1" == "-D" ]; then
BINARY=`find /var/containers/Bundle/Application/ |grep "$2.app/$2"|tail -n1|cut -d'/' -f-8|cut -d'.' -f-2`
echo "\"$BINARY\" path found!!"
else
count=`ps axwww|grep "$2"|grep container|grep '.app'|grep -v grep |wc -l|sed 's/ //g'`
if [ "$count" != "1" ]; then
echo "[!] \"$2\" was not uniquely found, please check your criteria."
exit 1
fi
PID=`ps awwwx|grep "$2"|grep container|grep '.app'|grep -v grep|sed 's/^\ *//g'|cut -f1 -d\ `
bad=1
case "$PID" in
''|*[!0-9]*) bad=1 ;;
*) bad=0 ;;
esac
if [ "$bad" != "0" ]; then
echo "[!] Process not found for string \"$3\""
exit 1
fi
fi
declare -a DYLIBS
if [ "$3" == "-l" ]; then
FEATURE=""
DYLIBS=("$4")
else
FEATURE="$4"
case "$FEATURE" in
cycript)
DYLIBS=(dylibs/cycript.dylib dylibs/cycript-runner.dylib)
;;
decrypt)
DYLIBS=(dylibs/bfdecrypt.dylib)
;;
test)
DYLIBS=(dylibs/simple.dylib)
;;
ispy)
DYLIBS=(dylibs/iSpy.dylib)
;;
iSpy)
DYLIBS=(dylibs/iSpy.dylib)
;;
default)
help
exit 1
;;
esac
fi
#
# Be a good netizen and tidy up your litter
#
function clean_up {
if [ -d "$DYLIB_DIR" ] && [ "$DYLIB_DIR" != "/System/Library/Frameworks" ]; then
rm -rf "$DYLIB_DIR" >/dev/null 2>&1
fi
rm -f "$RANDOM_NAME" > /dev/null 2>&1
rm -f /electra/usr/local/bin/bfinject4realz > /dev/null 2>&1
rm -f /electra/usr/local/bin/jtool.liberios > /dev/null 2>&1
}
#
# Entitlements for dylib injection and for our injector binary.
#
if [ ! -f entitlements.xml ]; then
cat > entitlements.xml << EOF
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>platform-application</key>
<true/>
<key>get-task-allow</key>
<true/>
<key>task_for_pid-allow</key>
<true/>
<key>com.apple.system-task-ports</key>
<true/>
</dict>
</plist>
EOF
fi
#
# Detect LiberiOS vs Electra
#
if [ -f /electra/inject_criticald ]; then
# This is Electra >= 1.0.2
echo "[+] Electra detected."
mkdir -p /electra/usr/local/bin
cp jtool.liberios /electra/usr/local/bin/
chmod +x /electra/usr/local/bin/jtool.liberios
JTOOL=/electra/usr/local/bin/jtool.liberios
cp bfinject4realz /electra/usr/local/bin/
INJECTOR=/electra/usr/local/bin/bfinject4realz
elif [ -f /bootstrap/inject_criticald ]; then
# This is Electra < 1.0.2
echo "[+] Electra detected."
cp jtool.liberios /bootstrap/usr/local/bin/
chmod +x /bootstrap/usr/local/bin/jtool.liberios
JTOOL=/bootstrap/usr/local/bin/jtool.liberios
cp bfinject4realz /bootstrap/usr/local/bin/
INJECTOR=/bootstrap/usr/local/bin/bfinject4realz
elif [ -f /jb/usr/local/bin/jtool ]; then
# This is LiberiOS
echo "[+] Liberios detected"
JTOOL=jtool
INJECTOR=`pwd`/bfinject4realz
else
echo "[!] Unknown jailbreak. Aborting."
exit 1
fi
#
# Do the actual injection into the remote process
#
for DYLIB in ${DYLIBS[@]}; do
if [ ! -f "$DYLIB" ]; then
echo "$DYLIB" doesn\'t exist
clean_up
exit 1
fi
# Use random filenames to avoid cached binaries causing "Killed: 9" messages.
RAND=`dd if=/dev/random bs=1 count=16 2>/dev/null | md5sum`
RANDOM_NAME="${INJECTOR%/*}/`dd if=/dev/random bs=1 count=16 2>/dev/null | md5sum`"
DYLIB_DIR="/System/Library/Frameworks/${RAND}.framework"
DYLIB_PATH="$DYLIB_DIR/$RAND.dylib"
# We'll give the injector as a random filename
cp "$INJECTOR" "$RANDOM_NAME"
chmod +x "$RANDOM_NAME"
#
# Find the full path to the target app binary
#
if [ "$1" != "-D" ]; then
BINARY=`ps -o pid,command $PID|tail -n1|sed 's/^\ *//g'|cut -f2- -d\ `
fi
if [ "$BINARY" == "COMMAND" ]; then
echo "[!] ERROR: PID $PID not found."
clean_up
exit 1
fi
echo "[+] Injecting into '$BINARY'"
#
# Get the Team ID that signed the target app's binary.
# We need this so we can re-sign the injected .dylib to fool the kernel
# into assuming the .dylib is part of the injectee bundle.
# This allows is to map the .dylib into the target's process space via dlopen().
#
echo "[+] Getting Team ID from target application..."
TEAMID=`$JTOOL --ent "$BINARY" 2> /dev/null | grep -A1 'com.apple.developer.team-identifier' | tail -n1 |sed 's/ //g'|cut -f2 -d\>|cut -f1 -d\<`
if [ "$TEAMID" == "" ]; then
echo "[+] WARNING: No Team ID found. Continuing regardless, but expect weird stuff to happen."
fi
#
# Move the injectee dylib to a sandbox-friendly location
#
mkdir "$DYLIB_DIR"
cp "$DYLIB" "$DYLIB_PATH"
#
# Thin the binary so that it's not FAT and contains only an arm64 image
echo "[+] Thinning dylib into non-fat arm64 image"
$JTOOL -arch arm64 -e arch "$DYLIB_PATH" >/dev/null 2>&1
if [ "$?" == "0" ]; then
rm -f "$DYLIB_PATH"
DYLIB_PATH="${DYLIB_PATH}.arch_arm64"
else
echo "[!] WARNING: Wasn't able to thin the dylib."
fi
#
# Sign platform entitlements and Team ID into our dylib
#
echo "[+] Signing injectable .dylib with Team ID $TEAMID and platform entitlements..."
$JTOOL --sign platform --ent entitlements.xml --inplace --teamid "$TEAMID" "$DYLIB_PATH" > /dev/null 2>&1
if [ "$?" != "0" ]; then
echo jtool dylib signing error. barfing.
clean_up
exit 1
fi
#
# Sign the randomly-renamed injector binary with platform entitlements
#
$JTOOL --sign platform --ent entitlements.xml --inplace "$RANDOM_NAME" >/dev/null 2>&1
if [ "$?" != "0" ]; then
echo jtool "$RANDOM_NAME" signing error. barfing.
clean_up
exit 1
fi
#
# Inject!
#
"$RANDOM_NAME" "$PID" "$DYLIB_PATH"
done
#
# EOF
#
echo "[+] So long and thanks for all the fish."
clean_up
exit 0
but I got the following error...
"/var/containers/Bundle/Application/7DE84F56-92EF-4775-AAE2-5FEA030400DC/7wonders.app/7wonders" path found!! [+] Electra detected. [+] Injecting into '/var/containers/Bundle/Application/7DE84F56-92EF-4775-AAE2-5FEA030400DC/7wonders.app/7wonders' [+] Getting Team ID from target application... [+] WARNING: No Team ID found. Continuing regardless, but expect weird stuff to happen. [+] Thinning dylib into non-fat arm64 image [+] Signing injectable .dylib with Team ID and platform entitlements... [bfinject4realz] Calling task_for_pid() for PID 0. [bfinject4realz] ERROR: task_for_pid() failed with message (os/kern) failure! [+] So long and thanks for all the fish.
What shall I do?
#50
 Posted 12 July 2018 - 04:58 AM
Posted 12 July 2018 - 04:58 AM

What shall I do?
app has to be able to run on device while cracking.
if the stock app crashes you obviously have a problem
#51
 Posted 12 July 2018 - 04:58 AM
Posted 12 July 2018 - 04:58 AM

yep ghostbin link does not work
#52
 Posted 12 July 2018 - 05:12 AM
Posted 12 July 2018 - 05:12 AM

yep ghostbin link does not work
just download it from github.
signer: https://github.com/Sacmunraga/signer
bfinject_mod: https://github.com/S...aga/sacmunCrack
#53
 Posted 12 July 2018 - 05:16 AM
Posted 12 July 2018 - 05:16 AM

just download it from github.
signer: https://github.com/Sacmunraga/signer
bfinject_mod: https://github.com/S...aga/sacmunCrack
Not for me to long winded need a simpler faster all in one method
#54
 Posted 12 July 2018 - 05:21 AM
Posted 12 July 2018 - 05:21 AM

Not for me to long winded need a simpler faster all in one method
my hair has already turned grey
#55
 Posted 12 July 2018 - 05:24 AM
Posted 12 July 2018 - 05:24 AM

Will do a lot of work for basically nothing
#56
 Posted 12 July 2018 - 05:30 AM
Posted 12 July 2018 - 05:30 AM

Will do a lot of work for basically nothing
you do realize it only takes a minute to crack on os11
#57
 Posted 12 July 2018 - 05:43 AM
Posted 12 July 2018 - 05:43 AM

you do realize it only takes a minute to crack on os11
looking at instructions looks to long winded then many do not work anyway not worth the time and effort. Something new anti cracking in https://itunes.apple...d971858273?mt=8Feral Fury it reboots your device when trying to carck so you need to rejailbreak tried 5-6 times on ios 10.2 and ios 9.3.1 Give up on it
#58
 Posted 12 July 2018 - 07:15 AM
Posted 12 July 2018 - 07:15 AM

app has to be able to run on device while cracking.
if the stock app crashes you obviously have a problem
I downloaded from iPhoneCake
https://www.iphoneca...530090434_.html
I then moved the app into iPAD with putty connected via FTP and installed with appinst from Cydia. I'm using Electra 1.4 and an iPad Pro2.
App is installed, but after run it crashed after the initial scene. I do understand that this is because the app is not signed correctly or because it's cracked with old method, not compatible with iOS11.
So can't I do anything in this case?
#59
 Posted 12 July 2018 - 07:58 AM
Posted 12 July 2018 - 07:58 AM

One thing for sure was cracked the old way as that cracker does not crack for ios 11 and has not cracked for a long time I know was angry about a leech ( TyToV )on this site reposting his cracks on other sites
#60
 Posted 12 July 2018 - 08:19 AM
Posted 12 July 2018 - 08:19 AM

One thing for sure was cracked the old way as that cracker does not crack for ios 11 and has not cracked for a long time I know was angry about a leech ( TyToV )on this site reposting his cracks on other sites
I don't understand if it's technically possible to do something or not.
Almost all the app I downloaded from AppCake and that worked on iOS9 with jailbreak are not usable on iOS11 with Electra and they crash when you run them, so you don't have a PID --> This procedure cannot be used.
Can someone explain technically why and what needs to be done?




 This topic is locked
This topic is locked